Recently I had the pleasure of ordering, installing, and configuring some new Ubiquiti UniFi network products, including a switch, wireless access points, and more! Today, I will review the Ubiquiti UniFi line of products for you!
My company Digitally Accurate Inc. is an Ubiquiti reseller, and we have Ubiquiti product in inventory and stock in our Vancouver and Toronto warehouses. Contact us if you’re looking at purchasing any Ubiquiti gear in Canada!
There are plenty of pictures below! 🙂
Update – March 20th 2020
It’s been just over 8 months now and I’m still in love with and highly recommend the UniFi hardware! It’s been working great, I’ve had no issues with any firmware updates or UniFi Controller updates, and it’s been rock solid!
The only problem I’ve experienced is an issue auto-negotiating 10Gig links with the SFP+ to 10GBase-T module. Forcing 10G on the server resolved this issue permanently.
I’m excited to add even more UniFi equipment to my network! Please enjoy this Ubiquiti UniFi Review!
The back story
For some time I’ve been wanting to replace a bunch of aging networking equipment at my company. This includes switches and wireless access points, and I wanted to consolidate the number of pieces of networking equipment I used. No more daisy chaining switches!
- Wireless
- First off, up to date I have been re-purposing consumer grade wireless routers as access points. While this has worked by disabling the router functions, DHCP, and DNS, it’s still not ideal. I wanted a true managed wireless solution. I always wanted proper coverage and no dropped connections.
- Switching
- Secondly, I’ve also been using a number of cheap daisy chained 8-port network switches. The amount of cables I use is absolutely crazy, the power-bar space for the transformers is crazy, and this is just crazy dumb! I wanted a true business/enterprise class manageable network switch that could handle all the cabling requirements my business has with all it’s servers, SANs, NASs, and other equipment.
- Multiple Networks
- Third, I’ve been using the multiple switches to maintain 4 different isolated networks across my virtualization stack. It would be ideal to implement VLANs on VLAN capable hardware, to consolidate, and ease management of the environment.
- 10Gb Requirement
- Fourth, I do require some 10Gb capabilities. While my servers are using multiple SFP+ DAC cables to direct-connect to the SAN, I still have numerous unused 10GBASET NICs and ports on my servers that I’d like to use. It would be fantastic if I could use this as a backhaul to a switch.
The Goal
Ultimately I wanted a business/enterprise class networking solution, that could handle all my wireless and networking needs, in an easy to manage way, and in an affordable way that wouldn’t break the bank.
After researching a number of vendors, weighing the pros/cons, I found the answer: Ubiquiti UniFi
Ubiquiti UniFi
Ubiquiti UniFi is a portfolio of enterprise grade products including wireless technologies, network switching, cloud management capabilities, and other hardware technology.
UniFi offers the latest technologies at affordable prices. They also allow you to integrate with the cloud, or keep everything separate and centrally managed on your own hardware and software.
The UniFi products support a number of enterprise technologies you’d normally find in enterprise gear, such as central management, VLANs, multi-SSID wireless, Guest WiFi access, Captive Portal, and way more!
They also have a beautiful switch line up consisting of numerous different port options, PoE options, and uplink options (SFP, SFP+, etc).
The Solution
So, after making the decision to switch to Ubiquiti UniFi, I spec’ed out the hardware I wanted to purchase. See below for the items I ordered:
- 1 x Ubiquiti UniFi Switch 48 (Part# US-48)
- 1 x Ubiquiti UniFi nanoHD (Part#: UAP-nanoHD)
- 2 x Ubiquiti 10GBASE-T SFP+ CopperModule (Part#: UF-RJ45-10G)
I ordered the equipment from my Vancouver warehouse (as mentioned before, my company has stock in Vancouver/Toronto), and waited!
2 days later, the equipment arrived…
I was very impressed with the packaging! Even opening the products, you were actually “presented” with the products. Very nicely done Ubiquiti!
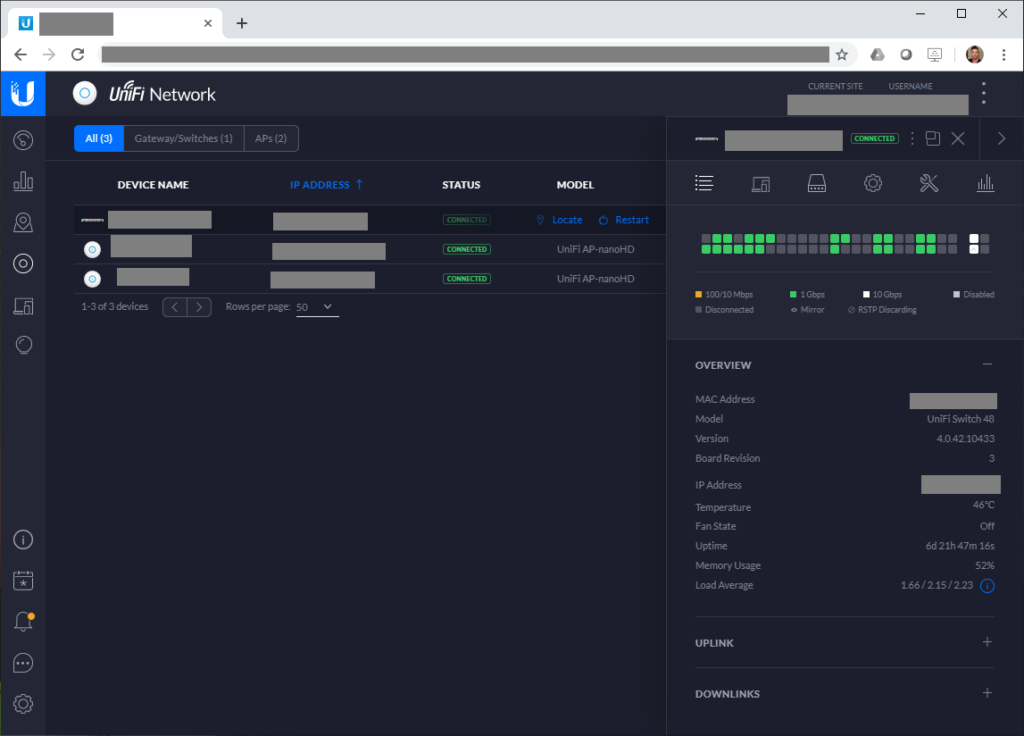
Ubiquiti UniFi Switch 48
The UniFi Switch 48, provides 48 x 1Gb standard ports, along with 2 x 10Gb SFP+ ports, and 2 x 1Gb SFP ports.
You can order this switch with multiple PoE options, however I ordered the non-PoE version.
The switch has 70Gbps of non-blocking throughput, and 140Gbps of switching capacity.
The switch does have fans, however I haven’t heard them come on except for the initial power-up test.
The SFP+ modules do run hot (hot to the touch), however after doing research I found out this is completely normal. There is a number of SFP+ and SFP module options that you can populate the ports with on the switch.
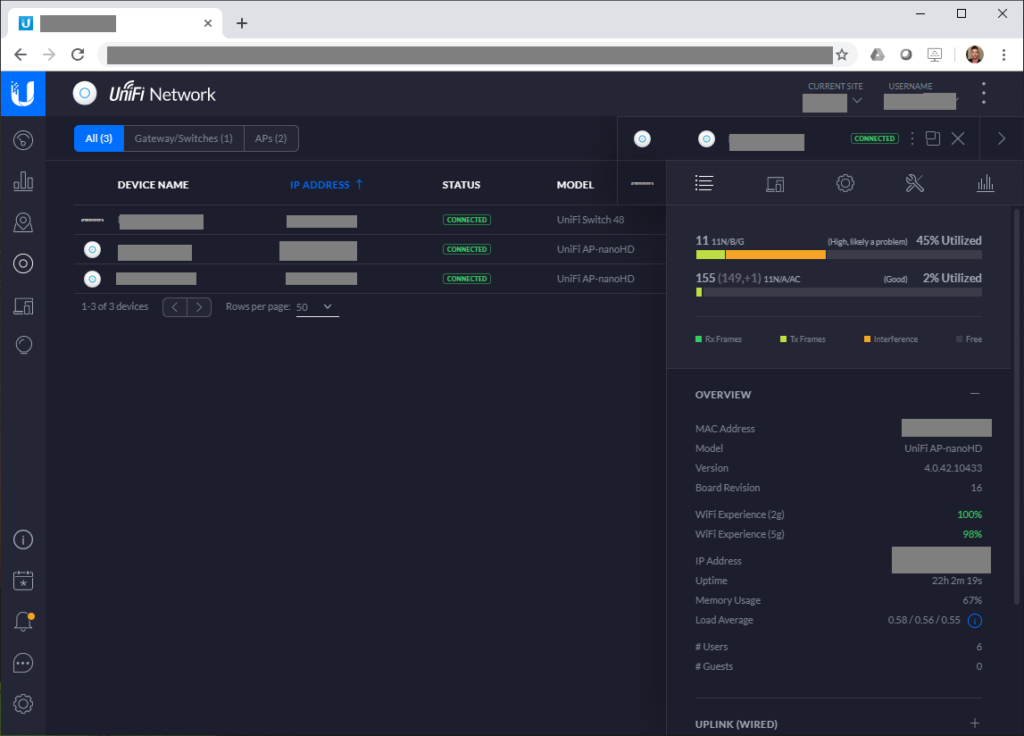
Ubiquiti UniFi nanoHD
The UniFi nanoHD wireless access point is a compact (smaller than the other UniFi APs) 802.11ac Wave2 device with MU-MIMO technology.
The unit is powered via PoE and is designed for roof mounting, although works great on a wall, or sitting on a desk.
The single quantity SKUs (like the one I ordered) include a PoE injector as seen above, however the multi-quantity SKUs do not. You can either use the PoE injector, or power it via your switch if your switch supports PoE.
The unit also ships with a roof mounting bracket and a getting started flyer.
On the 5Ghz band, the unit has a maximum throughput of 1733Mbps (1.73Gbps), and the 2.4Ghz band has a maximum throughput of 300Mbps.
The nanoHD supports a maximum of 8 seperate SSIDs per radio.
Ubiquiti 10GBASE-T SFP+ CopperModule
The 10GBASE-T SFP+ CopperModule allows you to connect RJ45 10Gb copper ethernet to the SFP+ port on a switch. This allows you to connect devices or other switches that support 10Gb links over RJ45 ethernet.
Ubiquiti has a number of other SFP+ and SFP modules that you can use to populate your ports depending on your requirements.
UniFi Controller
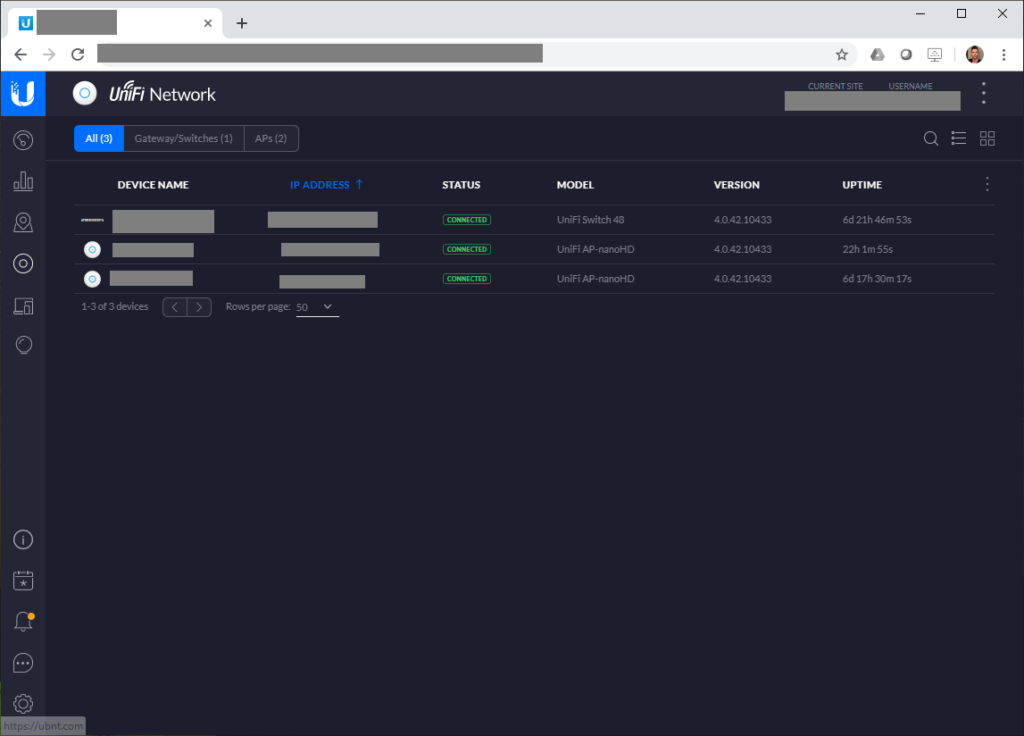
The UniFi controller is the software (or hardware) that controls and centrally manages all the UniFi products. In my specific environment, I deployed a virtual machine running Ubuntu Linux, installed the apt repo’s for the UniFi Controller, installed the UniFi controller, and then configured it.
You can also purchase a UniFi Cloud key, which is a hardware device that runs the UniFi controller software. This removes the need to deploy a computer, VM, or additional hardware to install the controller on.
Inside of the UniFi controller, you create your wireless networks, network profiles, network switch port profiles, and other configuration, so that it can be easily provisioned to hardware as you add it and expand your network.
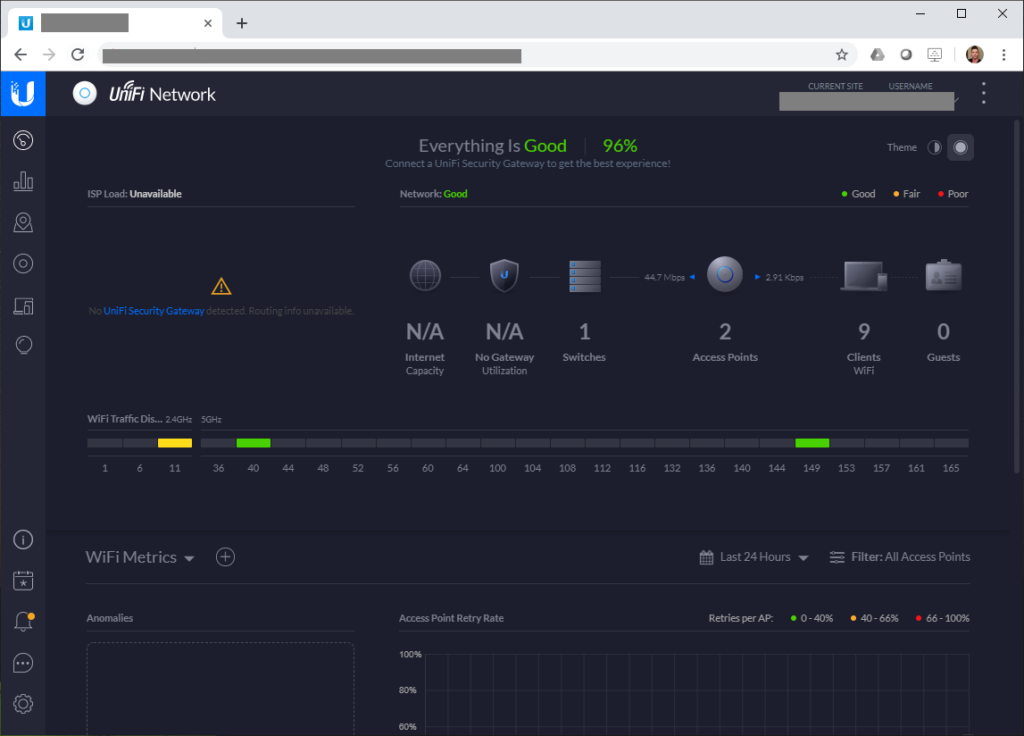
My Configuration, Notes, and Observations
For my configuration on the UniFi controller, I configured 9 VLANs, 4 SSID wireless networks, and numerous switch profiles for aggregation (via LACP).
When bringing the switch online, the profiles were provisioned and I could attach the profiles to individual network ports, or groups of ports. I could also override these profiles and manually set aggregation, VLAN IDs, trunking, etc if need be.
Since I’m using VLANs and want to configure multiple SSIDs, I need to have the wireless access points connected to a VLAN trunk, so that each network is available to be broadcast by the nanoHD APs. Since I configured the VLAN and network profiles earlier, this was instantly deployed automatically as I powered them on. If you had a simple network and didn’t use VLANs, none of this would be necessary and you’d be up and running in minutes.
Inserting the 10GBASE-T CopperModule in to the SFP+ ports on the switch, they were instantly detected. Connecting my 2 HPE DL360p Servers using Cat6, I was able to establish a 10Gb link with both servers instantly. The connection has been rock solid since for over 7 days. These connections are used as a VLAN trunks to my VMware vSphere instance. I also have a secondary connection from each server at 1Gb as failover (standby).
Enabling Jumbo frames was easy, and Ubiquiti UniFi fully supports it. While I couldn’t find out the exact MTU, I do know it’s around 9000. I’m assuming they allotted slightly more to account for the extra bytes due to VLAN tagging.
Overall Review
Overall, I’m extremely happy and impressed with the product. I’d definitely recommend this to clients, as well as friends and family.
The features and functionality make this product perfect for any business. And with the price point and ease of management, this equipment would be suitable for home and power users as well!
Not only did I get up and running in no time with an extremely complicated configuration, but it’s been rock solid now for over 7 days. If you had a simple configuration, you could have the equipment deployed in minutes.
What I liked the most:
- Wireless Speed
- Easy Switch Port Configuration
- Easy Wireless/SSID Deployment and Configuration
- Ease of Management (really easy yet extremely powerful)
- Monitoring and Statistics inside of UniFi Controller
- E-Mail notifications of rogue APs and other alerts
- Visibly beautiful hardware
- PoE injectors are included with single quantity AP SKUs
- Product lineup available
- Smartphone app for Android/iOS (Configure, Monitor, Deploy)
- Reliable 10Gb on the CopperModule SFP+ 10GBASE-T Modules
Getting back to basics, the equipment has filled all the requirements I originally had and than some, I’m extremely happy!
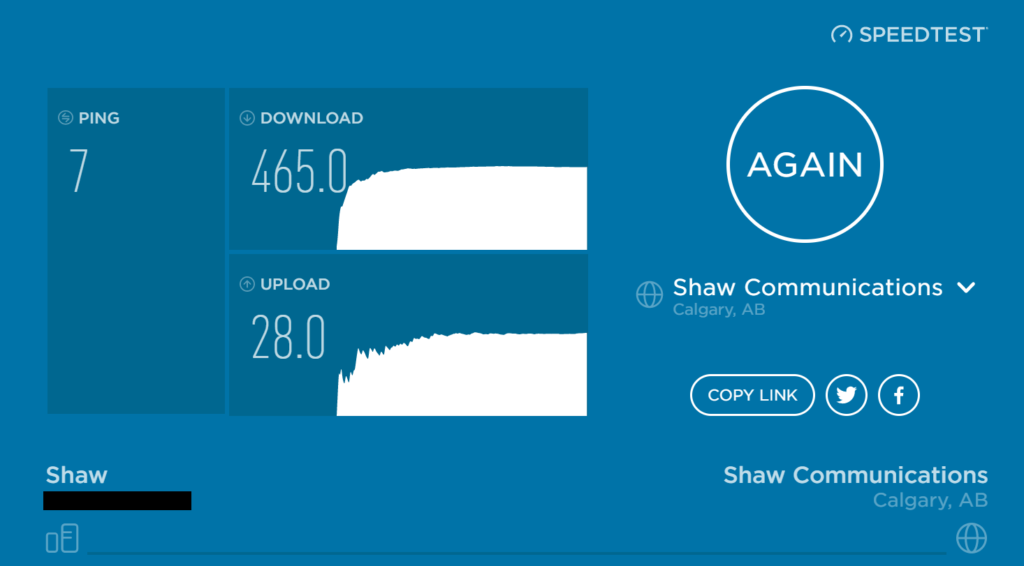
And I almost forgot to mention, the wireless is FAST! Absolutely no complaints. I’ve posted a speed test below, please note I’ve achieved way faster accessing content internally, however this was limited by my internet connection at the time.
I’m actually looking forward to purchasing some more equipment, my shopping list includes:
- More nanoHD APs for coverage
- Possibly a couple UniFi HD In-Wall units for testing
- 2 x UniFi Switch 16 XG for SAN connectivity
- 4 x UniFi Switch 8 (150W) for remote cable drops and PoE
Hope this review helps if you’re considering Ubiquiti! And remember, I’m a re-seller so I can offer some very attractive pricing on this equipment!
Additional Resources and Blog Posts:
- Going 10Gig with the Ubiquiti UniFi US-16-XG Switch
- Ubiquiti UniFi US-8 Gigabit Switch
- Change management VLAN on Ubiquiti UniFi Hardware and Controller
- The Best UniFi Device Adoption Method
Manufacturer Product Links