I’ve had my main web server directly on the net for some time now. The box runs CentOS and I always have it fully up to date, with a minimal install just to act as a web server.
It’s always concerned me a little bit, the fact is I keep the box up to date as much as possible, but it’s still always in the back of my mind.
This weekend I had some time to mess around with some stuff. I wanted to get it setup behind my Sophos UTM, however I did NOT want it to use the public IP address that it’s setup for as I have numerous static IPs all for different services.
I spent a good 3-4 hours doing lots of searching on Google, and Astaro.org. I saw a few people that wanted to do the same thing as me, but didn’t really find an explanation for anything.
Ultimately I wanted to setup another external IP address on the Sophos UTM software appliance box, and have that external IP dedicated to JUST the web server. Everything else would continue to run as configured before I started modifying anything.
I finally got it going, and I thought I would do a little write up on this since I saw a lot of people were curious, however no one was having luck with it. So far I’ve just done it for my main web server, however in the future I’ll be doing this with a few more external IPs and servers of mine. So let’s log into the Astaro web interface and get started!
PLEASE NOTE: I performed this configuration on Astaro Security Gateway Version 8, this will also work on a Sophos UTM
- Configure the additional IP – “Interfaces & Routing”, then choose “Interfaces”. Select the “Additional Addresses” tab on the top of the screen. Hit the “New additional address…” button and configure the additional IP. Please note this worked for me as all my static IPs use the same gateway for the most part, if you have multiple statics that use different gateways this may not work for you. In my case I called this address “DA-Web”. Make sure you enable this afterwards by hitting the green light!
- Configure the NAT Rules – On the left select “Network Security”, then choose the sub item “NAT”. We do not want to touch anything under “Masquerading” so lets go ahead and select the “DNAT/SNAT” tab. In this section we need to create two rules, one for DNAT, and one for SNAT. Keep in mind that “Full NAT” is available, but due to the setup of the traffic initiation I don’t think we want to touch this at all.
- Create the DNAT Rule – Hit the “New NAT rule” button. Set “Position” to Top”. “Traffic Source” and “Traffic Service” to “Any”. “Traffic Destination” set to the additional address you created (keep in mind this has the same name as the main external, only with the name of the connection inside of it). Set “NAT mode” to “DNAT”. And finally set Destination to the server you want this going to, or create a new definition for the server. Make sure “Automatic packet filter rule” is NOT checked. See image below for my setup.
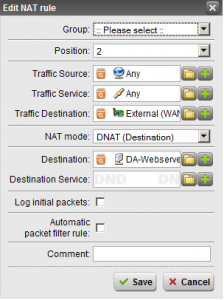
- Create the SNAT Rule – Hit the “New NAT rule” button. Set the “Position” to top. “Traffic Source” should be set to the definition you created for the server you are doing this for. “Traffic Service” should be “Any”. “Traffic Destination” should be “Internet”. Keep in mind this is very important, we want to make sure that if you use multiple subnets inside your network that SNAT is ONLY performed when needed when data gets shipped out to the Internet, and NOT when your internal boxes are accessing it. Set “NAT mode” to SNAT. And finally “Source” being the additional IP you created (again this looks like your normal External IP, but hold the mouse over when selecting the definition to make sure it’s the “additional” IP you created). Make sure “Automatic packet filter rule” is NOT checked. See image below for my setup.
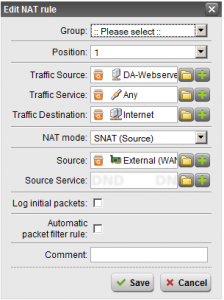
- Create Packet Filter Rules – Now it’s time to open some ports up so that your server can offer services to the internet. This is fairly standard so I’m sure that you can do it on your own. In my example I created a few rules that allowed HTTP, DNS, and FTP from “any” using the service, to the destination “DA-Webserver” to allow the traffic I needed.
- Create the DNAT Rule – Hit the “New NAT rule” button. Set “Position” to Top”. “Traffic Source” and “Traffic Service” to “Any”. “Traffic Destination” set to the additional address you created (keep in mind this has the same name as the main external, only with the name of the connection inside of it). Set “NAT mode” to “DNAT”. And finally set Destination to the server you want this going to, or create a new definition for the server. Make sure “Automatic packet filter rule” is NOT checked. See image below for my setup.
This should be it, it should be working now. If you don’t want to create the packet filter rules and want ALL traffic allowed, you can simply forget section c above, and when creating the DNAT and SNAT rules check the “Create automatic packet filter rules” box on both rules. Keep in mind this will be opening your box up to the internet!
If you find this useful, have any questions, or want to comment or tell me how to do it better, please leave me a comment!
Thanks!
Thank you so much for this how to. Saved me a migraine from trying to figure this out.
Well done.
Nelson
Great post. I was amazed to find the lack of information regarding this standard firewall feature. Thanks for the explanation and screen shots.
Hey! Im setting up my own Astaro Security Gateway and having a few troubles. I cant access my webserver from its external address. Before, I had the standard Linksys and all the port forwarding set up just fine. I tried following your procedure but I keep getting a 403 Error. Anyway, I was wondering if you would be willing to help me out? I wanted to ask before I wrote all my specs down. Thanks! Paul
Very thorough and complete description, thanks!
I have a question regarding the “new external IP” you are using to communicate with your server. I have one external IP address (assigned by the telcom provider). Now, is your “new external IP” an additional, different IP address? Or is it just a new Astaro interface definition using the same (and only) external IP address? I assume the latter, but I’m not sure that’s how you have done it.
Thanks,
Klaus
I actually have numerous Static IPs I pay for from my ISP…
The ASG is configured with its own static, and then I have the “Additional” static IPs which I use for 1 to 1 NAT…
The primary internet interface has it’s own static IP, and then I used the “Additional Address” tab to configure the other IPs. I guess you could use all the different IPs to contact the astaro, but I have it disabled on my setup. The other IPs are strictly for web servers, etc…
I’m not sure, but I’m thinking you may be confusing this tutorial for simple port forwarding. Only use 1-to-1 NAT if you actually have numerous different IPs from your ISP….
If you only have one IP for your ASG, and want to do simple forwarding the procedure is totally different. All you need to do is configure your webserver on your LAN, configure the ASG both LAN and internet interfaces, then simply create the DNAT rule (which does the forwarding), and to keep things simple, choose “Automatic packet filter rule”. This will do the trick 🙂
Thanks again. One more question: what benefits do separate IP addresses give you? Better security? Is your web server in a LAN with the other machines behind the firewall?
I actually have two separate firewalls configured. One that handles all of the servers (which does One-to-One NAT for numerous external Static IPs to numerous internal servers I run), and a separate firewall for all internal traffic (which uses a dynamic IP and has an ISP assigned hostname which somewhat lightly anonymizes my traffic).
I just like to have things seperate, incase there is a problem, or any type of security breach. Lot’s of companies have 15+ servers being behind one or two single IP addresses, but I just don’t like it.
[…] […]
Thanks Steve… another person helped by this blog post! Now our mail server is sending out messages from the right IP.
The “Source Service” field was particularly confusing to me, and I wasn’t sure if leaving it blank was okay (as it apparently is).
No Problem!
Glad it helped. It actually is kind of very confusing. Even when I did this above myself I wasn’t sure if it was going to work or not. But I’ve been using this config for over a year now and no problems whatsoever!
Stephen
Thanks for this post. I been wanting to create a 1-to-1 NAT correctly but was having some problems. I have been using just DNAT with the firewall rules but have since changed to using your example. The only problem I’m still having is when I go to http://www.whatismyip.com it shows my gateway ip address instead of the additional ip address I created. Do you have any ideas how to correct this?
Hi Kerry,
Just curious, do you have your web security enabled on the Astaro device? If so, Astaro will intercept your web traffic and since it’s acting as a “proxy” it will show the IP address of the proxy server (which in our case is the main IP configured on the Astaro Security Gateway).
I did a little test just now to confirm this. I logged on to my web server which is configured for 1-To-1 NAT correctly, I opened up http://www.whatismyip.com and it displayed the wrong IP. I logged on to the ASG, and disabled web security. After doing this I reloaded the IP page, and it changed and now showed the correct external IP of the configured 1-to-1 NAT.
You should perform the test above, just to make sure your rules are configured correctly. If you experience the same behavior as above, you have nothing to worry about and everything is fine. Just make sure you turn web security back on!
Hope this helps,
Stephen
Stephen,
Thank you for helping out here and sorry about the delay in responding back to you. I tried what you said and bingo that was it. I turned off the web filtering and was able to get the correct ip address reported back from http://www.whatismyip.com. I mainly wanted to make sure the email servers were reporting back the correct ip address for reverse dns and spf filtering. Thanks again for your help
Kerry
[…] […]
Hey Stephan,
In a roundabout way I am trying to accomplish the same thing. I have an ASG425 v7 on the edge of our network. We have an additional MicroTik router on our internal network that is servicing an additional network that is administered by their own tech support. This routers WAN interface is fully accessible from our internal network and I can login to it with no problems on its static(internal) address when I am on the local network. I have used your scenario to NAT one of our available public IPs the the routers WAN(internal static) IP and have had no luck gaining even ping access.
1st
Create an additional address with the public IP which is then pingable from the internet.
2nd (position 2)
Create a rule Any -> Any -> Additional external (address) -> DNAT -> Internal definition, no auto PFR
3rd (position 1)
Creat a rule Internal definition -> Any -> Internet -> SNAT -> Additional external (address), no auto PFR.
honestly I can’t create any 1:1 open NAT for any interfaces so far. If this thread is still alive I can supply additional information. Any help is greatly appreciated.
Hi Richard,
First and foremost, a ping (ICMP packets) in this type of setup will still be replied from the device with the IP itself. It doesn’t matter if you have 1-to-1 NAT configured, the first device (in your case the outside ASG router) will be the one replying to the ping if you ping it from the internet. The only way to change this is if you start creating specific rules for ICMP packets (which is something most people wouldn’t want to do, and I’ve never done it). I’m a bit rusty with this, but I’m sure ICMP packets don’t fall under standard NAT rules, in fact they aren’t touched at all…
Also, something to note is that usually by default, ICMP requests (pings) are disabled on the Astaro Security Gateyway. You need to turn this on inside of the UI. No matter what, if you have ICMP turned on, you should be able to ping the public accessible internet IP of your ASG box IF you have ICMP packets turned on.
It’s always important when working on this stuff to troubleshoot in layers or tiers, and start from the side where it’s easiest to troubleshoot. Make sure each layer is working before moving on to the next.
One more important mention, keep in mind that NAT/SNAT/1-to-1 all modify the packets. If you setup a rule for translation for internet communication to internal, there’s a chance that in some cases internal-to-internal communication might be altered. Always make sure that when accessing a service internally or testing, that you test from the internet coming in, and internally separately. If you already know all this, just ignore it, what I typed above might help others…
So moving on to your setup:
Do you have firewall rules enabled to allow communication on some ports? We need to first make sure that it’s not working at all. As I mentioned above, ICMP ping packets aren’t a good way of doing this. Is the Microtik router running a simply service on port 80 (web)?
If it is, I’d try accessing it. If it doesn’t work, I’d check to make sure you have all the firewall rules enabled for communication…
Let me know, and I’ll see if I can help further…
Stephen
By the way,
I just wanted to let everyone know that I recently took a backup from this config, installed Sophos Unified Threat Management (UTM) version 9 and restored the config… While version 9 properly supports 1 to 1 NAT, I just wanted to let everyone know that this way still works, and after restoring my configuration everything worked perfect (nothing broke).
Stephen
[…] […]
Hi Stephen
Just wanted to thank you for a great guide. I was faced with the very same problem.
I wasn’t excited abut the idea of spending hours figuring this. Until i came across your guide – very simple and clear. All worked 1st time.
Thanx again
Hi,
Thanks for the tutorial. I’m still confused as how you setup the additional interfaces. Please clarify:
1. Is the DA-Webserver configured to use the External IP?
2. What is the “Ext WAN”? Which IP does it use and is it the same IP for DA-Webserver?
Hi Edwardson,
1. The “DA-Webserver” is configured to use it’s own external IP which is seperate from the external IP that the Astaro/Sophos device is using… In the tutorial, it’s the interface you created in step 1. In my case it’s called “External (WAN) [DA-Web]”.
2. “External (WAN)” is the typical external IP that Astaro uses. “External (WAN) [DA-Web]” is the IP that my “DA-Webserver” uses.
Keep in mind the screenshots block out the text to the right of “External (WAN)”. It actually says “External (WAN) [DA-Web]”. It’s the separate external IP I created specifically for the “DA-Webserver”.
Hope this helps,
Stephen
is it possible to configurr a DNAT on ASTARO, knowing that the Traffic Destination is a VLAN interface (not a physical interface).
Hi Bouchouka,
Yes it is possible. You just need to make sure you have your proper network interfaces (and VLANS) configured properly on Astaro. Then simply just use the proper network device definition when creating the rules.
Stephen
I have to do a SNAT for IPSec VPN. The client want us to NAT our source to 172.24.1.77. How would I do this? I am new to Sophos.
Hi Jonathan,
Sorry for the late reply. Just curious, did the instructions above not work?
[…] found this online Astaro Security Gateway – SNAT, DNAT, 1-to-1 NAT and Full NAT – HowTo Astaro Security Gateway – SNAT, DNAT, 1-to-1 NAT and Full NAT – HowTo | The time I've wa… dose this how-to apply to me now that I use UpLink Balancing and Multipath Rules ? I have static […]
hi,
i am having a mail server running behind astaro security gateway.
i am able to send mails from my mail server to external domains but not able to receive mails from external domain like yahoo,gmail etcc…my local domain mails are sent and reecived smooth.i don;t run a dns server,can you help me out.
Hi Gayathri,
Can you confirm if the incoming e-mails are at least hitting the Astaro Security Gateway?
Hi,
I’m not sure if you still read this, but I’ll give it a try.
I tried to follow your instructions. I created the two NAT rules and checked “automatic packet filter rules”, so there shouldn’t be any issue on that side.
I also ticked “Initial packets are logged”, and I can see the DNAT rule appearing in the logs whenever I try to access my additional IP address from outside.
The IP address in the URL bar changes to the home URL of my web server (with the internal IP address, that is).
But then, I cannot access the webpage.
Do you know what could be the problem?
Could it be a protocol issue?
Thanks!
Mat
Actually, I can connect, but it’s really slow, and most of the time, I get a ERR_CONNECTION_TIMED_OUT
It seems like it’s coming from the firewall, because the server is really fast internally.
Any idea of what might cause this?
Thanks!
Hi Mat,
DO NOT check the “automatic packet filter rules” box, you’ll need to make your own rules as I’m guessing this is considered a complex non-standard setup. This may or may not be causing your issues.
Also, I could be wrong, but logging initial packets may cause some performance related issues, but again, I could be wrong.
When you mentioned the address bar changes to the home URL, do you have code in the web server that’s redirecting it to a different site/service?
Also, did you make sure all the proper definitions/hosts/addresses were configured when creating the rules on the Sophos UTM?
Cheers,
Stephen
Hi
i face a problem with 1:1nat i want mail server outging to be from a second external interface .i configured nat as you advice above but it didnt work when i use whatismyaddress.com site.if i turn off web filter as you advice how i will open my web sites and how i will test with whatismyaddress site .
thanks
Hi Walaa,
If you turn off the web filter, all it will do is turn off the proxy on the device, this means web traffic will passed un-scanned, which means it will work, just not scanned for viruses.
Stephen