It’s been coming for a while: The requirement to deploy VMs with a TPM module… Today I’ll be showing you the easiest and quickest way to create and deploy Virtual Machines with vTPM with NKP (Native Key Provider) on VMware vSphere!
As most of you know, Windows 11 has a requirement for Secureboot as well as a TPM module. It’s with no doubt that we’ll also possibly see this requirement with future Microsoft Windows Server operating systems.
While users struggle to deploy TPM modules on their own workstations to be eligible for the Windows 11 upgrade, ESXi administrators are also struggling with deploying Virtual TPM modules, or vTPM modules on their virtualized infrastructure.
With the Native Key Provider (NKP) on VMware vSphere, you can easily deploy a key provider, enabling vTPM (Virtual Trusted Key Platform) enabled Virtual Machines.
What is a TPM Module?
TPM stands for Trusted Platform Module. A Trusted Platform Module, is a piece of hardware (or chip) inside or outside of your computer that provides secured computing features to the computer, system, or server that it’s attached to.
This TPM modules provides things like a random number generator, storage of encryption keys and cryptographic information, as well as aiding in secure authentication of the host system.
In a virtualization environment, we need to emulate this physical device with a Virtual TPM module, or vTPM.
What is a Virtual TPM (vTPM) Module?
A vTPM module is a virtualized software instance of a traditional physical TPM module. A vTPM can be attached to Virtual Machines and provide the same features and functionality that a physical TPM module would provide to a physical system.
vTPM modules can be can be deployed with VMware vSphere, and can be used to deploy Windows 11 on ESXi.
Deployment of vTPM modules, require a Key Provider on the vCenter Server.
For more information on vTPM modules, see VMware’s “Virtual Trust Platform Module Overview” documentation.
Deploying vTPM (Virtual TPM Modules) on VMware vSphere with NKP
In order to deploy vTPM modules (and VM encryption, vSAN Encryption) on VMware vSphere, you need to configure a Key Provider on your vCenter Server.
Previously (but still an option), this would be accomplished with a Standard Key Provider utilizing a Key Management Server (KMS), however this required a 3rd party KMS server and is what I would consider a complex deployment.
VMware has made this easy as of vSphere 7 Update 2 (7U2), with the Native Key Provider (NKP) on the vCenter Server.
The Native Key Provider, allows you to easily deploy technologies such as vTPM modules, VM encryption, vSAN encryption, and the best part is, it’s all built in to vCenter Server.
Enabling VMware Native Key Provider (NKP)
To enable NKP across your vSphere infrastructure:
- Log on to your vCenter Server
- Select your vCenter Server from the Inventory List
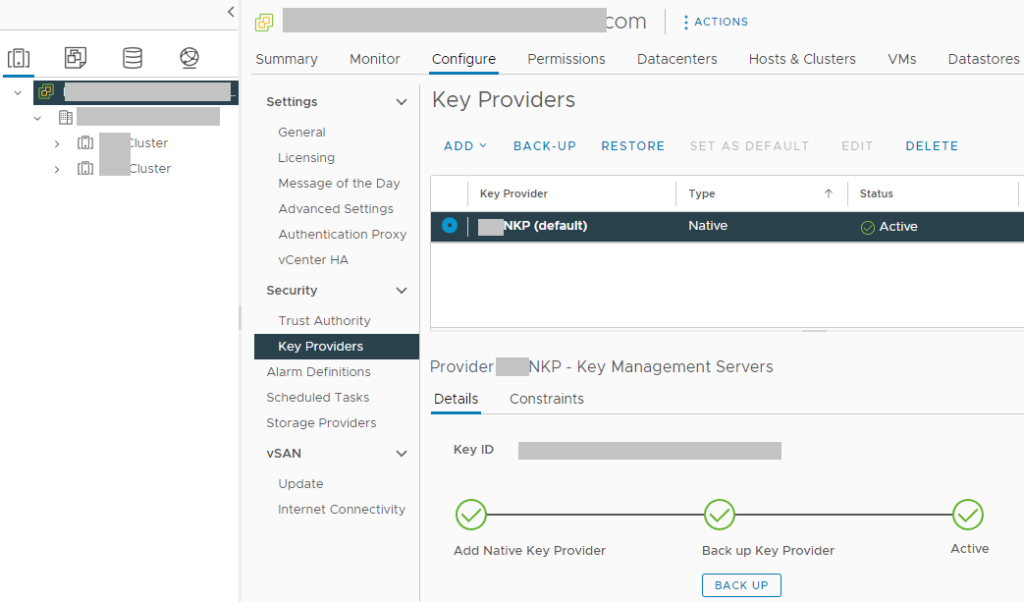
- Select “Key Providers”
- Click on “Add”, and select “Add Native Key Provider”
- Give the new NKP a friendly name
- De-select “Use key provider only with TPM protected ESXi hosts” to allow your ESXi hosts without a TPM to be able to use the native key provider.
In order to activate your new native key provider, you need to click on “Backup” to make sure you have it backed up. Keep this backup in a safe place. After the backup is complete, you NKP will be active and usable by your ESXi hosts.
There’s a few additional things to note:
- Your ESXi hosts do NOT require a physical TPM module in order to use the Native Key Provider
- Just make sure you disable the checkbox “Use key provider only with TPM protected ESXi hosts”
- NKP can be used to enable vTPM modules on all editions of vSphere
- If your ESXi hosts have a TPM module, using the Native Key Provider with your hosts TPM modules can provide enhanced security
- Onboard TPM module allows keys to be stored and used if the vCenter server goes offline
- If you delete the Native Key Provider, you are also deleting all the keys stored with it.
- Make sure you have it backed up
- Make sure you don’t have any hosts/VMs using the NKP before deleting
You can now deploy vTPM modules to virtual machines in your VMware environment.
This is a very helpful and informative site for those looking to clarify complicated operations in a virtual environment.
Thank you for this, helped me a lot. Appreciate it!
This worked for me on ESXi 8.0 for a Win2019 Server.
Hello,
thanks for this information. I have one question. Can i add a Native Key Provider in my Cluster when not all ESXi Host has a Hardware TPM Module?
Thank you
Christopher
Hi Christopher,
Physical TPMs are not required when rolling out vTPM with the Native Key Provider.
However, if you do have physical TPMs in your hosts, they can provide additional security and functionality.
Cheers,
I have Use key provider only with TPM protected Esxi hosts (Recommended) checked when we added native key provide, and now it gives error when testing VTPM on a test VM. So, what is the best way to uncheck that setting??
Hi Pratika,
If you have already deployed it and your hosts do not have TPM, you may need to deploy another NKP provider that allows hosts that do not have TPM.
Please be cautious with this, as if you create a new key provider, you’ll need to re-key. If any of your VM’s have been encrypted, you will lose access if you delete without re-keying.
Please see: https://core.vmware.com/native-key-provider-questions-answers for more information.
Cheers,
Stephen
Can you do this with vSphere Essentials Plus or do you need the full up license
Hi Tom,
All versions of vSphere 7 and newer are licensed to use vTPM and NKP.
With Native Key Provider, decryption keys are stored locally on ESXi hosts.
What’ happend if the host is physicaly stolen ?
Can the data be accessed by the attacker ?
If I want to protect my data against theft, should I use TPMs and store the keys in the TPM instead of on the boot devices ?
So with vTPM enabled Disaster Recovery to another vCenter cluster is not possible?
Hi Mark,
With vTPM, DR is possible, however you’ll need to make sure the other vCenter instance has the NKP (or 3rd party key provider) configured.
In the case of NKP, as long as the key provider is configured, it should be able to run any VMs created with the NKP instance.
Cheers,
Stephen
Thx for your info, helpful! I found out that when not making the NKP the default key provider the TPM option is not available when trying to add to new or existing VM. So if anybody else get this: make sure it’s always selected as default 😉
I followed the instructions successfully using vSphere 8. It appears while it’s possible to create a Windows 11 VM successfully. I could encrypt the VM config files but not the drive itself. Did I miss a check box somewhere or is that a limitation of vTPM?
Hi Gear,
Enabling vTPM encrypts the VM file and enables a vTPM, but this does not enable VMDK disk encryption. Any additional encryption capabilities must be manually enabled.
In my scenario above, for the pull-down choice under
Select Storage
Encrypt this virtual machine
I selected “VM Encryption Policy” and maybe that is where I should have selected “Management Storage Policy – Encryption” instead to encrypt the entire VM.
Another mentionable is on one vSphere 8 with ESXi 8, I have Windows 11 as a pull-down choice for “Guest OS Version”, whereas on a second vSphere 8 with ESXi 7, I only have Windows 10. Not sure if that is because of the ESXi 7 or not.
Thank you for this article. It was/is the clearest explanation of steps to follow to create Windows 11 in vSphere.
Are you trying to deploy vTPM or perform disk encryption? They are two different functions (however related as they use host encryption).
I successfully deployed W11 with the VSphere Native Key Provider for a vSphere 8 and ESXi 8, and with a vSphere 8 and ESXi 7.
I then enabled MS BitLocker to encrypt the disks.
I believe there’s nothing else. Thanks again for the article.
[…] Stephen Wagner: Create and Deploy Virtual Machines with vTPM and NKP on VMware vSphere […]
[…] Stephen Wagner: Create and Deploy Virtual Machines with vTPM and NKP on VMware vsphere […]
Hi Stephen.
I hope you are doing well and thank you for providing a comprehensive video for deploying Win11 VDI.
I followed your instruction to create gold image. I have an issue deploying VDI desktop. when i configure Desktop Pool to add VTPM automatically, creating VDI fails with the following error on VM
a required file is missing or contains errors.
File: \Windows\system32\winload.efi
Error code: 0xc000000f
but when I add VTPM manually after VM fully generated I have no problem.
could you please help me with that?
Thanks in advance
Hi Ahmad,
Is this for persistent full-clone VMs, or non-persistent Instant Clones?
Cheers,
Stephen